Platforms and Languages Leveraged:
- Windows 10: Virtual Machines (Microsoft Azure)
- EDR Platform: Microsoft Defender for Endpoint
- Kusto Query Language (KQL)
- Tor Browser
Scenario
Management suspects that some employees may be using TOR browsers to bypass network security controls because recent network logs show unusual encrypted traffic patterns and connections to known TOR entry nodes. Additionally, there have been anonymous reports of employees discussing ways to access restricted sites during work hours. The goal is to detect any TOR usage and analyze related security incidents to mitigate potential risks. If any use of TOR is found, notify management.
Indicators of Compromise Discovery Plan
- Check "DeviceFileEvents" for any tor(.exe) or firefox(.exe) file events.
- Check "DeviceProcessEvents" for any signs of installation or usage.
- Check "DeviceNetworkEvents" for any signs of outgoing connections over known TOR ports.
Step 1. Search the "DeviceFileEvents" Table
Searching this table shows any logs related to files being created, renamed, deleted, etc. Searching the DeviceFileEvents table for any string containing "tor" should locate event logs associated with the TOR browser. In order to show the relevant machine we need to narrow our search down to the specific "DeviceName" in question in this case "tyler-windows10". In our query we want to show relevant information that will aid us in our investigation. To do this, I projected the following: time the event was generated, the name of the device, which action took place, file info (name and path),SHA256 hash(for integrity purposes), and the user who did the action.
Query Used to locate events:
DeviceFileEvents
| where DeviceName == "tyler-windows10"
| where FileName contains "tor"
| order by TimeGenerated desc
| project TimeGenerated, DeviceName, ActionType, FileName, FolderPath, SHA256, Account = InitiatingProcessAccountName
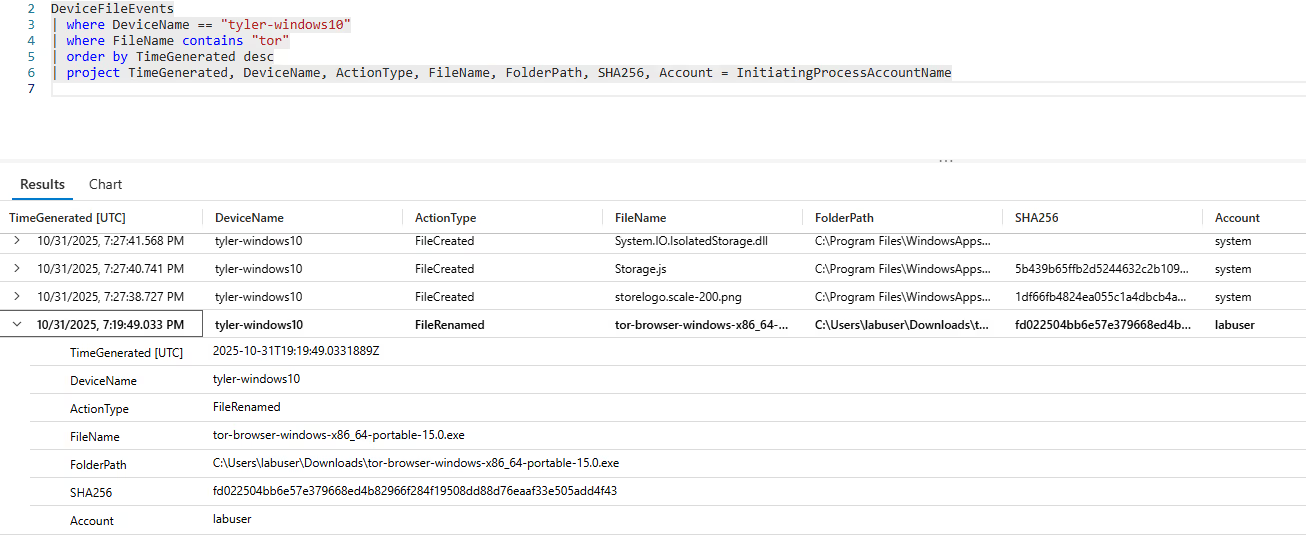
Our query results not only showed a TOR executable being downloaded, but it was renamed shortly after "tor-browser-windows-x86_64-portable-15.0.exe". These events began at: 2025-10-31T19:19:49.0331889Z.
To investigate this further, I changed the query to add the "IntiatingProcessCommandLine" to see if I could find additional relevant information.
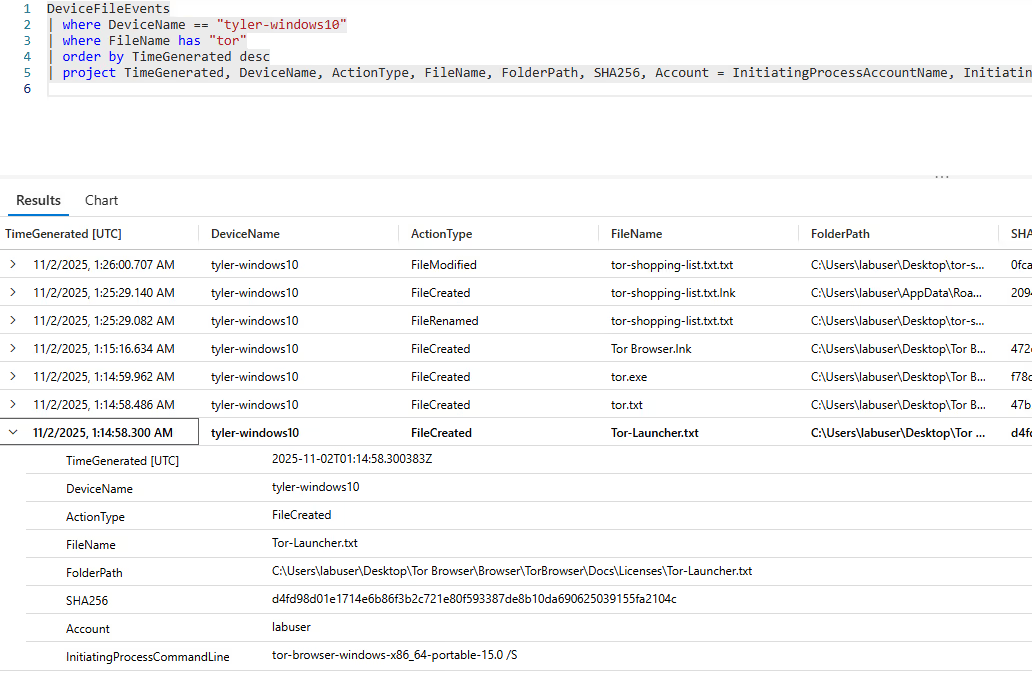
After the query, I noticed a "Tor-Launcher.txt" , which at face value would imply that the TOR file was executed. By examining the event further, we see the "InitiatingProcessCommandLine" shows the exact same executable being run with a "/S" switch at the end. This shows that the user used a silent installation to be more stealthy as this avoids user prompts, reducing the chances of a manual detection. This is definitely something to take note of.
Step 2. Searched the "DeviceProcessEvents" Table
After learning about the users actions, the next step is to see if the user actually opened the browser. To do this we can query the "DeviceProcessEvents" table, to show any processes or applications that were started. To check all common process names of the tor browser, I check to see if the "FileName" contains "tor.exe", "firefox.exe" (Tor is a modified version of firefox), or "tor-browser.exe".
Query Used to locate events:
DeviceProcessEvents
| where DeviceName == "tyler-windows10"
| where FileName has_any ("tor.exe", "firefox.exe", "tor-browser.exe")
| project TimeGenerated, DeviceName, AccountName, ActionType, FileName, FolderPath, SHA256, ProcessCommandLine| order by TimeGenerated desc
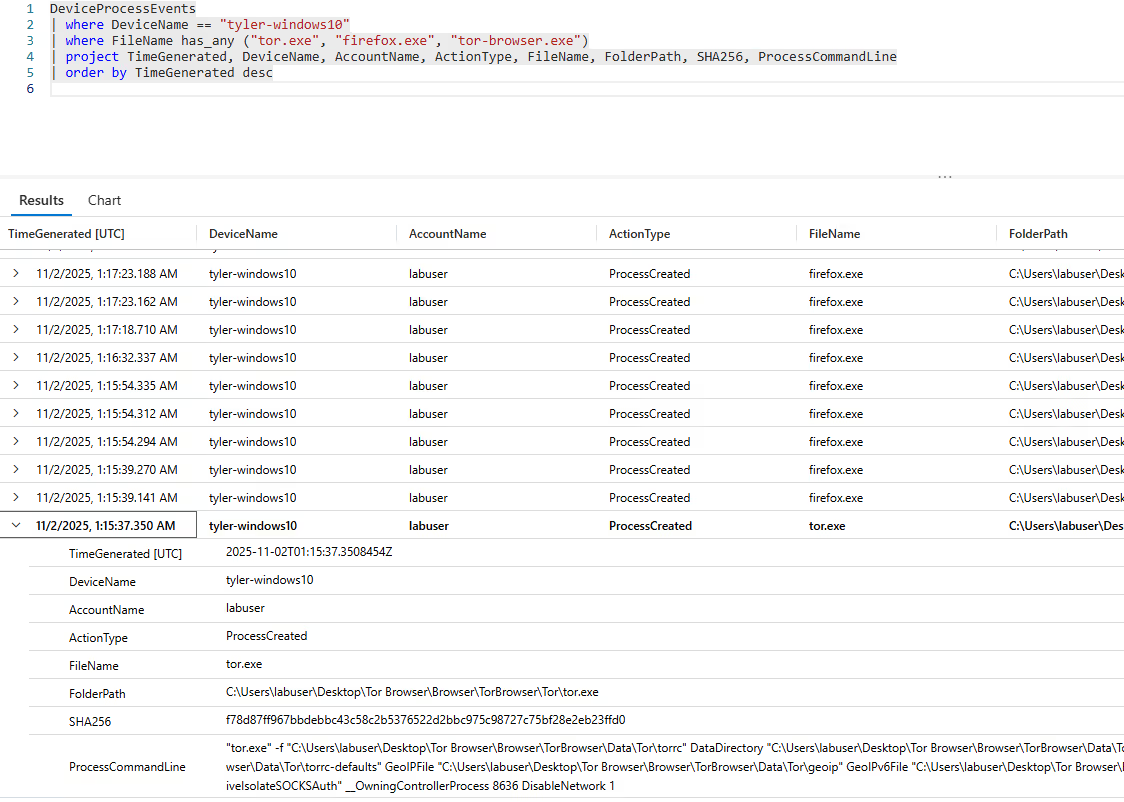
There was evidence that the user did open a process called "tor.exe" at 2025-11-02T01:15:35. There were several other instances of firefox.exe and tor.exe spawned after this timeframe as well.
Step 3. Searched the "DeviceNetworkEvents" Table
After confirming the user downloaded and opened the Tor browser, the next best approach in the investigation is to see what websites the user was visiting. It is important to note that Tor browser is associated with many illegal activities such as buying and selling drugs, weapons, or other illegal content. the browser connects to the tor network by using a system of encrypted nodes allowing for the user to be anonymous online. With this in mind, we need to query for common ports of these nodes to showcase which sites and IP addresses they were connecting to. It is also best to include normal HTTP and HTTPS ports in our query to get the full picture of the user's behavior, as the user could have been browsing the web with no nefarious actions taking place.
Query Used to locate events:
DeviceNetworkEvents
| where DeviceName == "tyler-windows10"
| where InitiatingProcessFileName has "tor"
| where RemotePort in ("9001", "9030", "9040", "9050", "9051", "9150", "443", "80")
| project TimeGenerated, DeviceName, ActionType, InitiatingProcessAccountName, RemoteIP, RemotePort, RemoteUrl, InitiatingProcessFileName, InitiatingProcessFolderPath
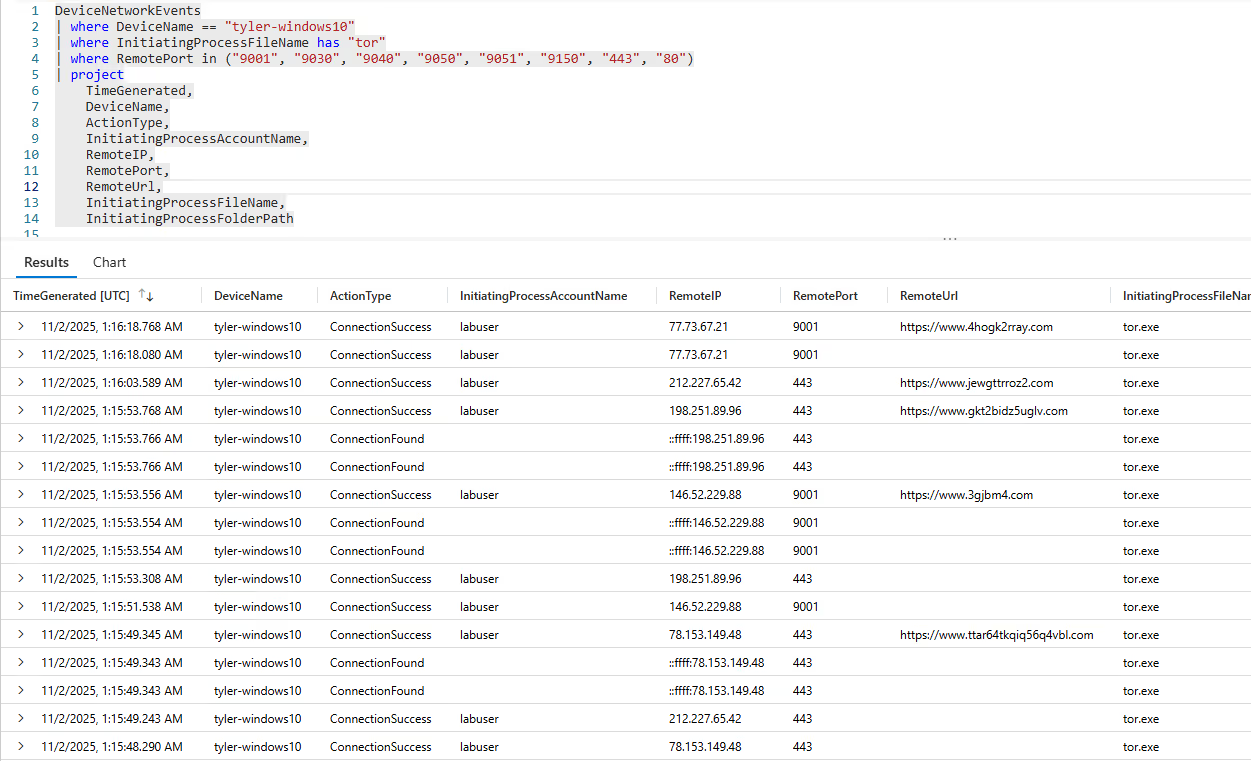
The query results show multiple connections to "RemotePort" 9001, indicating the user was connected to the tor network, which is against the company's acceptable use policy.
Chronological Event Timeline
2025-10-31T19:19:49.0331889Z — File events discovered by hunting: a search for files containing “tor” shows the user downloaded the Tor installer at this time. The installer filename was tor-browser-windows-x86_64-portable-15.0.exe (SHA256 fd022504bb6e57e379668ed4b82966f284f19508dd88d76eaaf33e505add4f43).
2025-11-02T01:14:40.9956149Z — Process created: the user account labuser executed the downloaded portable Tor installer on device tyler-windows10 using the command tor-browser-windows-x86_64-portable-15.0 /S, triggering a silent installation from C:\Users\labuser\Downloads\tor-browser-windows-x86_64-portable-15.0.exe.
2025-11-02T01:15:31.0800000Z — Tor Browser opened: evidence shows labuser launched the browser (process spawns recorded for tor.exe and firefox.exe). Multiple subsequent launches of browser-related processes were observed and Tor bundle files appeared under a Desktop path such as c:\users\labuser\desktop\tor browser\browser\torbrowser\tor\tor.exe. A Desktop file named tor-shopping-list.txt was created around this timeframe.
2025-11-02T01:16:18.0808086Z — Network connection established: tor.exe on tyler-windows10 successfully connected to remote IP 77.73.67.21 on port 9001 (a known Tor relay port), confirming the Tor process was actively communicating on the Tor network. Additional Tor-related outbound connections were observed in the same timeframe, including some over TCP 443.
Summary
the user 'labuser' on device 'tyler-windows10' downloaded a Tor portable installer, silently installed it, launched the Tor Browser (bundle files copied to Desktop and tor-shopping-list.txt created), and then used Tor to establish outbound connections including to 77.73.67.21:9001, confirming installation and active use of the Tor network from the endpoint.
Response Taken
TOR usage was confirmed on endpoint "tyler-windows10" by the user "labuser". The device was isolated and the user's direct manager was notified.

%201.svg)



